As a kid, I absolutely loved Encyclopedia Brown, Nancy Drew and Sherlock Holmes. What I really loved most about them was how they caught the bad guy… it was different every time! One of the things that always caught my attention was how secret codes were constructed.
Cryptography is the writing and decoding of secret messages, called ciphers. Now for governments these secret ciphers are a matter of national security. They hire special cryptanalysts who work on these ciphers using cryptanalysis. If you practice encoding and decoding ciphers, you too can become a really great cryptanalyst.
Now I’m going to share with you my favorite collection of secret codes and ciphers that I've collected over the years, and you can use them to send secret messages to your friends.
Rail Fence Cipher
In this video, I’ll show you how to use the Rail Fence Cipher. Before you start, say this three times fast: cryptanalysts use cryptanalysis to crack ciphers!
How did you like the Rail Fence Cipher? Pretty neat, right? Would you rather encode or decode a cipher? I think both parts are fun. But if you’re encoding, just make sure the decoder knows the correct formula to use!
Practice time! Write the cipher of the following message:
- COME TOMORROW AT 2PM
- HE HAS ARRIVED AT THE AIRPORT
- HE IS CARRYING A BAG
- THEY ARE HERE NOW
- COME AT MY PLACE
Shift Cipher
Shift ciphers were used by Julius Caesar in Roman times. The key is a number which tells you how many letters you’ll shift the alphabet. These are fairly simple to encode and decode. However, you have to be extra careful when encoding because mistakes can throw off the decoding process. Watch the video to see why it’s important to double check your work!
Do you see why it’s important to double check the encoding? This is a simple code, but it’s easy to shift and end up with a jumble when your message is decoded. So always check your cipher with a practice decoding prior to sharing it.
Use the key shift number 4 on the letters of alphabet to code or decode:
- I LOVE MATH
- SAWNA HAWRE JCXQZ
- LHAWO AYKIA QKZWU
- I AM THREE FEET TALL
Date Shift Cipher
The Date Shift cipher is a much harder code to break than, for example, the more simple Shift cipher. This is because the shift number varies from letter to letter, and also because it’s polyalphabetic (this means that a single number can represent multiple letters). I’ll explain it all in the video.
What do you think about the Date Shift cipher? The possibilities for numerical keys are endless. You can use the date you’re sending the message, birth dates, phone numbers, and more! Just remember to start decoding by writing the key numbers over the top of the encoded cipher. And always makes sure the decoder has the correct numerical key!
- COME TO MY HOME : March 16th 2023
- THEY HAVE JUST LEFT : June 1st 2012
What are the original messages? (These messages were sent on July 16th 1992)
- GUBZC GOGNZ
- MKFZV GAZTO GROZQ
Twisted Path Cipher
In this video, I demonstrate a Twisted Path Cipher. It uses a matrix and a path in order to encode your message. The shape of the path you create within the matrix of a Twisted Path Cipher determines how difficult it will be to break the code. Watch the video to learn exactly how it works.
Remember that it will be easier to break your code if you use straight lines, so consider using some extra tricks to make it more difficult. For example, spirals, and zigzags are super hard to crack, and paths don’t have to be continuous! If you’re encoding, just make sure that the decoder knows the correct path shape (or shapes) to use!
Given the following message, what would be the best size of the table to use?
- COME TOMORROW
- WE ARE WAITING AT THE BUS STATION
- THE LETTER IS IN HIS BRIEFCASE
- HE WILL COME LATE TODAY
Pig Pen Cipher
The Pig Pen cipher is of the most historically popular ciphers. It was used by Freemasons a century ago and also by Confederate soldiers during the Civil War. Since it’s so popular, it’s not a very good choice for top secret messages. Lots of people know how to use this one! It starts with shapes: tic-tac-toe grids and X shapes. I really like it because coded messages look like they're written an entirely different language!
To make the cipher a little harder to crack, arrange the encoded message in groups of five characters. As always, remember that your intended recipient needs the Pig Pen key in order to decode your message.
Practice coding these messages:
- WAKE ME AT NOON
- KEY IS UNDER BLUE ROCK
Polybius Checkerboard Cipher
Polybius was an ancient Greek who first figured out a way to substitute different two-digit numbers for each letter. In the Polybius cipher we’ll use a 5x5 square grid with the columns and rows numbered. Take a look at the video and I’ll show you how it works.
To make the Polybius more difficult to crack, you can write the alphabet backwards or in an up and down pattern rather than left to right. Just be sure the decoder knows if you've used a different path or pattern to encode.
Encode the following statements using the Polybius Cipher grid from the main lesson:
- LET US LEAVE
- SHE IS HERE
- 32-35-35-31-11-45-45-23-15-45-11-12-32-15
- 24-45-24-44-23-24-14-14-15-34
Cracking Ciphers
Cryptograms are solved by making good guesses and testing them to see if the results make sense. Through a process of trial and error, you can usually figure out the answer. Knowing some facts about the English language can help you to solve a simple substitution cipher. For example, did you know that an E is the most commonly-used letter in the English alphabet? It’s also the most commonly-used letter to end a word. Watch the video below to learn some more tips and tricks to get you on the right track to being an expert cryptogram solver!
So, it helps to have a lot of words to work with so that you can begin to recognize patterns in the code. Here are some examples from the video:
- single letter words will most likely be either A or I
- the most frequent two-letter words in English are OF, TO, and IN
- the most frequently used three-letter words are THE and AND
- finally, the most frequently occurring four-letter word in English is THAT
Additional tips include the fact that Q is almost always followed by U, and that N often (but not always) follows a vowel. Finally, if two code symbols occur in a row, they could be a consonant combination such as LL, EE, SS, OO, TT, etc. The real trick to this is to try something, and then if it doesn't work, go back and try something else.
Playfair Cipher
This is a super hard cipher to break. It’s encoded by taking pairs of letters and numbers from a matrix. There are three rules to follow.
- If both letters are in the same row, then use the letters immediately to the right of each other. (Think of the rows as wrapping from the right end back around to that same row’s left end).
- If both letters are in the same column, then use the letters immediately below them. If necessary, the bottom letter wraps back around to the top of the same row.
- If the two letters or numbers are in different rows and in different columns, then each letter is replaced by the letter in the same row that’s also in the same column of the other letter. Basically, you find each intersection of the pair. Use the letter or number below the pair and then the one above the pair.
Play Fair sounds really complicated, but that also makes it a tough code to crack!
Remember: when decoding the Playfair cipher, you have to shift up instead of down and left instead of right. And it’s easy to make a mistake by encoding in the incorrect order. So always double check your cipher before sending it on to the recipient. Mistakes make messages much harder for the decoder to interpret!
Scytale Cipher Machine
In this video I’ll show you how to use a actual cipher machine called a scytale. This was first used in ancient Greek and Roman times, most notably by the Spartans.
To make a scytale, use a cylinder with a piece of paper wrapped around it. Then simply print your message in rows that run along the length of the cylinder.
When the paper is unwrapped, the message is scrambled! Watch the video and I’ll show you the trick to proper message decoding.
Paper Enigma Machine
Secret codes and ciphers are so much fun to learn about and create! This particular secret code machine is a simpler model of the original that was so complex, it took a brilliant mathematician, Alan Turing, to devise the techniques which cracked the code. In order to create this paper machine, you'll need the templates (listed below). Before you print and cut them out, watch the first part of the video, because you may have to re-size it so it will fit your container.
Materials:
- Pringles chip can (empty)
- Tape and scissors
- Color printout of the templates
How to Use the Machine:
1. Line up the fray bars on the reflector and input/output (this is your start position)
2. Decide on a 3-letter key. You can use ABC, CAT, DOG... any three you want. Write these down now.
3. Turn the rotors so that the three letters of your KEY are lined up.
4. What is the message you want to encode? Choose a short message to start with.
5. For each letter of your message, TURN ONLY THE RIGHT ROTOR one step towards you (to the letter in line with the gray alignment bar goes to the next one in the alphabet).
6. Do NOT turn the reflector or the input/output cylinders!
7. You need to turn it ONCE BEFORE you start encoding.
8. Now find the letter from your message on the input/output cylinder and trace it through all three rotors, reflector, and back through all three rotors and back to the input/output cylinder. Write down your encoded first letter!
9. Continue to work your way through your message, but before you finish, read steps 10-14 about Rotor Turnover.
Rotor Turnover
You'll notice that all three rotors have a shaded gray letter. This will help scramble up your message even more. Here's how to handle it:
10. If the middle rotor is gray, TURN ALL THREE rotors one step toward you (this may be easier to do one at a time).
11. If the letter on just the right rotor is gray, turn the MIDDLE AND RIGHT rotors one step toward you.
12. If none are gray, just turn the right rotor one step toward you.
13. The gray on the LEFT rotor is not used. It's there in case that rotor changes position to be a middle or right rotor in the future.
14. If you follow all the turnover rules, you might find that you have a gray shaded letter on the middle rotor that steps into position when turning over. If that happens, you need to DOUBLE STEP, meaning that ALL THREE ROTORS (not just the middle rotor) must step again when the next letter is processed.
Let's Practice with the Enigma Machine!
Use rotors I, II, & III and key A D S to decipher this message:
R Z F O G F Y H P L
You should end up with two words you recognize and the rotors at positions B F C.
Enjoy your enigma machine!
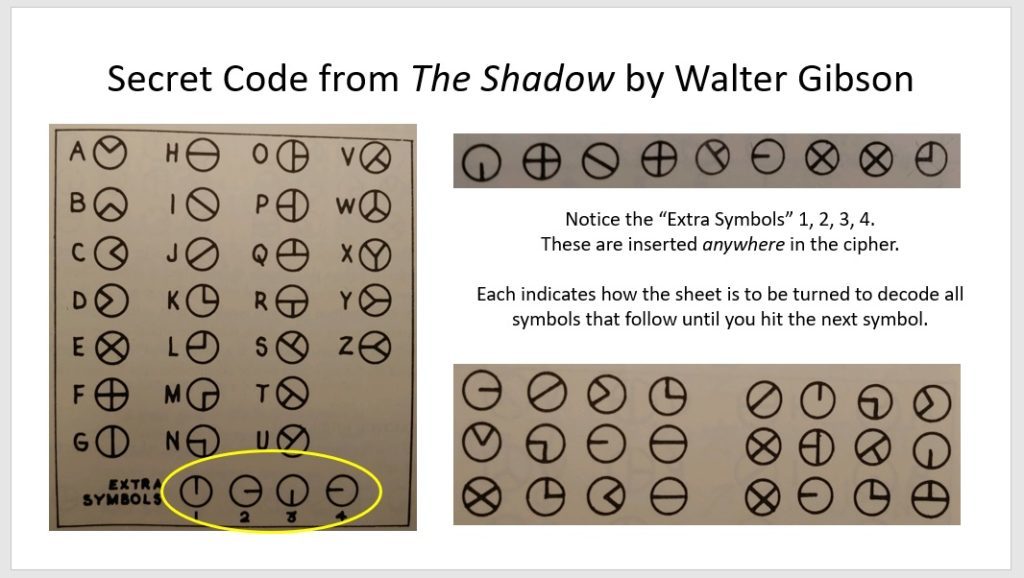
Bonus Cipher! The Shadow
Did you know that we also covered a special cipher back in Fractions Week #7 in the intermediate section of the live math class? This cipher from the 1930s is from a super-popular book (and radio) series that baffled kids and adults alike when they were published.